furb3t
Forero Novato
Sorry in advance, but I don't speak Spanish, so I'll write in English and then I'll translate with google translator the text.
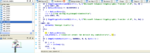
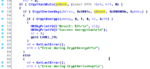
I'd like to analyze file upgrade.lgu but this file is packed; looking around in the www, I tried (on xda) a file lgu2dir but it's not able to unpack our file because the system is changed. I saw that jdk changed this file for his radiologos (2byte!?!?! is an address?!?!) so I ask to him if there a program or a way to unpack the lgu file and have all the structure visible.
Thanks
Translation with google translate.
Lo siento por adelantado, pero yo no hablo español, así que voy a escribir en Inglés y luego voy a traducir con google traductor el texto.
Me gustaría analizar el archivo upgrade.lgu pero este archivo está lleno; mirando alrededor en el www, he intentado (en xda) un archivo lgu2dir pero no es capaz de desempaquetar nuestro archivo porque el sistema se cambia. Vi que jdk cambiaba este fichero por sus radiologos (2byte!?!?! Es una dirección?!?!) Así que le pregunto si hay un programa o una forma de desempaquetar el fichero lgu y tener toda la estructura visible.
Gracias
I'd like to analyze file upgrade.lgu but this file is packed; looking around in the www, I tried (on xda) a file lgu2dir but it's not able to unpack our file because the system is changed. I saw that jdk changed this file for his radiologos (2byte!?!?! is an address?!?!) so I ask to him if there a program or a way to unpack the lgu file and have all the structure visible.
Thanks
Translation with google translate.
Lo siento por adelantado, pero yo no hablo español, así que voy a escribir en Inglés y luego voy a traducir con google traductor el texto.
Me gustaría analizar el archivo upgrade.lgu pero este archivo está lleno; mirando alrededor en el www, he intentado (en xda) un archivo lgu2dir pero no es capaz de desempaquetar nuestro archivo porque el sistema se cambia. Vi que jdk cambiaba este fichero por sus radiologos (2byte!?!?! Es una dirección?!?!) Así que le pregunto si hay un programa o una forma de desempaquetar el fichero lgu y tener toda la estructura visible.
Gracias